SCADA Security Basics: Why Industrial Networks are Different than IT Networks
October 2012 by Heather MacKenzie
Previously we looked at the question of “Why are PLCs so insecure?” Today we are going to come at SCADA security from another angle, which is “Why is securing Industrial Networks different than securing IT Networks?” We will also look at three ways to address these differences.
Recently I attended the Belden Industrial Ethernet Infrastructure Design Seminar and participated in an excellent session by Mark Cooksley, product manager for network management in Belden’s Hirschmann group, called “Introduction to Network Security”. It did a great job of explaining why Industrial Control Systems (ICS) are easy to attack, and it also explained high level solutions for securing them.
Industrial Control Systems are not IT Systems
“None of this would be a problem if those plant floor people just used proper security policies – what’s wrong with them?”
IT Manager after a Security Incident
Have you ever heard this?
Courtesy: Good Health Group
The heart of IT network systems is often a climate controlled, secured data center where the equipment is usually standardized and less than 10 years old. In contrast, the heart of ICS network systems is on the plant floor, often in a hazardous environment, and the average life of the equipment is more than 10 years.
This type of thought reflects a lack of understanding of the differences between IT and ICS networks. Now, while you might be fully aware of what they are, I will call them out in case you need a handy list for a future chat with an IT professional.
IT and ICS security solutions vary because each system has different:
– performance requirements
– reliability requirements
– operating systems and applications
– risk management goals
– security architectures
– security goals
and different assumptions about security, often incompatible ones.
In particular, the number one goal of IT security is rooted in the concern about privacy - “Protect the Data” whereas the number one goal of ICS security is based on the concern for safety “Protect the Process”.
Security Issues in Control Networks
Most ICS system security issues fall into 3 major categories.
1. Soft Targets
First of all, control networks are full of what we would call “soft” targets – devices that are extremely vulnerable to disruption through their network interface. The PCs in many plants run for weeks or months without any security updates, and some even operate without any anti-virus tools. In addition, many of the controllers in these networks were designed in an era when cyber security was not a concern; as a result, many of these devices can be disrupted by malformed network traffic or even by high volumes of correctly-formed traffic.
2. Multiple Pathways
Second, many control networks have multiple pathways through which cyber security threats can enter the plant. These pathways often bypass existing security measures in the plant, and some of them don’t even appear on a network diagram. For example, laptop computers that are carried in and out of facilities, or USB keys that move from one PC to another. These can easily bring malware into the plant and rapidly spread it from one system to another.
3. “Flat” Networks
Third, unfortunately many ICS networks are still implemented as large, “flat” networks with no isolation at all between unrelated subsystems. This means that if a problem does occur in one part of the plant, it can spread very quickly to other unrelated subsystems and even to remote plant sites.
Security Solutions
Mark presented 3 high level approaches to securing SCADA and ICS systems.
1. Harden the Perimeter
The idea of isolating the plant network from the office network with firewalls and a DMZ is nowadays just common sense. It’s a measure that you won’t have any trouble convincing your IT friends of. (Our sister company Hirschmann has excellent firewalls for this purpose.)
2. Defense in Depth
The concept of Defense in Depth is to go beyond having a security perimeter by having layers of defense throughout the control network. This way, if malware or inappropriate network traffic breaches the perimeter, it can be stopped and/or contained by defenses at other points in the system. For example, removable media used in the plant could introduce malware.
Our technology, the Tofino Industrial Security Solution is particularly designed for this purpose. It can be installed in live plant networks without plant downtime, it is industrially hardened, it secures industrial protocols and it is easy to configure by controls professionals.
An IT analogy for industrial Defense in Depth is the antivirus (AV) and personal firewall software that is installed on PCs. There are many reasons industrial control devices such as PLCs and DCS aren’t running security software, (not the least of which is there is no security software available for PLCs). Unfortunately, the lack of AV for controllers doesn’t mean a lack of security threats for PLCs, so in the industrial case it is preferred to use industrial firewalls.
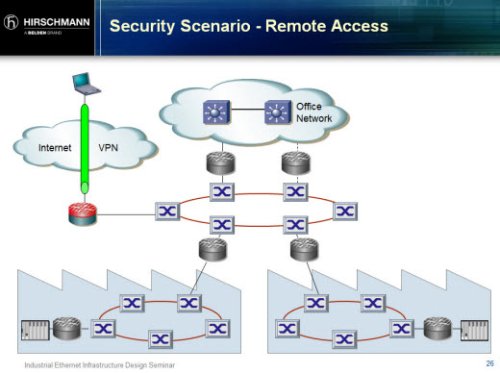
3. Remote Access
Another way that malware or inappropriate network traffic could penetrate the perimeter firewall is if certain people or machines are given remote access to do things like maintenance from another location (such as for an oil platform that is not easily accessible). In order to secure this type of connectivity, VPNs are recommended. This is a method that is commonly used by IT.
4. Other Recommendations
To further face the challenge of securing control networks, we also recommend:
following the best practices that we outlined in our joint White Paper with exida “7 Steps to ICS and SCADA Security”
learning and applying ISA IEC 62443 standards1
focusing security efforts on the “crown jewels” of your operation
Cyber Security Inertia is Still Common
During his presentation Mark told of many occasions when he had been called to client sites to help them with security, but unfortunately it was usually after they had experienced damages from a cyber incident, rather than beforehand.
Often people take the approach that if nothing has happened (or has been detected) previously, then nothing will happen now. The concept of leaving systems alone is attractive to many controls professionals.
Mark urged people who are thinking this way that it is not if, but when, a cyberattack will occur. He urged people to just get started, and to resist the idea that plant cyber security is complicated or that it has to cost a lot of money.
He closed his presentation with the Japanese proverb:
“When you are thirsty, it is too late to think about digging a well.”
Do you have any tips to share on how your organization got moving on ICS security? What about how to work effectively with IT? We look forward to your comments.
1 Formerly ANSI/ISA-99 Standards
Related Content to Download
Presentation - "Introduction to Network Security"
Download this 71 slide presentation and learn:
• The differences between IT and ICS systems and high level solutions for securing industrial networks
• What firewalls do and what they do not do
• The OSI Model and how different technologies secure different layers of it
• What VPNs are and the different types of encryption they use
Related Links
• ISSSource.com Webpage: Belden: Security Front and Center
• Blog: SCADA Security Basics: Why are PLCS so Insecure?
• Blog: SCADA Security: Tofino provides an Alternative to Patching
• Blog: Controlling Stuxnet – No More Flat Networks PLEASE. Let’s Embrace "Security Zones"
• White Paper: How Stuxnet Spreads – A Study of Infection Paths in Best Practice Systems







 Actu
Actu