Major Far Eastern human rights portal cracked to serve up malware - AlienVault
June 2012 by AlienVault
AlienVault’s research team have discovered a large human rights Web portal that has been compromised and is serving up malware to site visitors.
The ASEAN site compromise is notable as the portal is both high profile and may be linked to Google’s warnings on state-sponsored attacks, says Jaime Blasco - a researcher with the Security Information and Event Management (SIEM) solutions specialist – who adds the crack appears to centre around a Windows XML Core zero-day vulnerability (http://bit.ly/N2xxU2)
“Whilst this high-profile portal crack and consequent drive-by malware-fest is notable for being a possible hostile act by another government and/or its supporters, the fact that Windows flaw has been exploited so quickly and comprehensively proves the need for vigilance and understanding of zero-day flaws,” he said.
“It also, of course, underlines the need to patch your operating system as well as the applications software on a very regular basis, regardless of how large – or small – your computer systems estate is,” he added.
The AlienVault researcher went on to say that the CVE-2012-1889-linked vulnerability exploit on the ASEAN human rights portal appears to involve the same group as the site hacks reported by colleagues at Sophos.
Every time a page is displayed to the visitor, the content is modified and additional html code – in this case actual exploit code – is inserted dynamically to the user’s Web browser:
The malicious code, he says, checks the operating system version - as well as the Java Run Time Environment code – presented on the visitor’s computer, loading a payload delivery Flash file – Geoffrey.swf – if the visitor’s system is WinXP or Win7-powered.
The infection is also notable, he adds, because another file – icon.js – loads externally and interrogates the visitor’s computer for a wide variety of information – including details of which IT security/AntiVirus software that is running – which is then relayed to an remote Internet server.
Thanks to its research, AlienVault has extracted a variety of this interrogative information, including the following revealing screenshots:
Image 1: Compromised data – analysed by hacker on the basis of region
Image 2: Compromised data – analysed by hacker on the basis of Web browser used
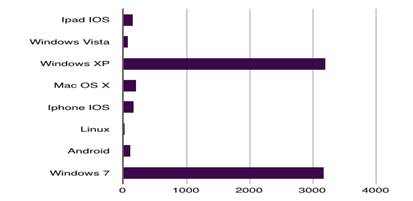
Image 3: Compromised data – analysed by hacker on the basis of operating system used
Blasco concludes that the number of state-sponsored incidents involving Southeast Asian Nations have been increasing in recent last months, especially when it comes to private sector (non-governmental) organisations.
“We have described a technique used by attackers to perform reconnaissance that gives them information about potential targets including software and Antivirus versions,” he says in his latest security posting.
This information can be used to perform future attacks on the victims. Being able to detect the Antivirus used by the victim within the browser opens new options when exploiting the system. The attacker can drop different payloads based on the detected Antivirus to evade detection,” he adds.
For more on the compromised Far Eastern ASEAN portal: http://bit.ly/LFiRdD







 Actu
Actu