Bradley Anstis, M86 Security: On Your Best Behaviour – Tackling Blended Threats in a Web 2.0 World
February 2010 by Bradley Anstis, VP Technical Strategy for M86 Security
A blended threat is described as any threat or attack that uses a combination of attacks against different vulnerabilities or through different methods. Early blended threats used a combination of viruses and application vulnerabilities to infect the user’s computer. The latest type of blended threat to emerge is one that uses a powerful combination of email and Web to deliver its payload and infect a user’s computer.
These Blended email attacks are one of the most successful attacks on the Internet today. In terms of volume, if we consider that daily M86 predict that there are in excess of 150 million spam messages sent and we have observed emails with links to malicious content being in excess of 30% of all spam you can see that this is a serious problem, especially given that the latest blended threats are more successful than ever. They are successful because the email message, very simple and well engineered, is difficult to detect as Spam. There is no attachment either which means there is nothing for the email gateway to scan. They infect using the Web channel which, typically, has next to no malware scanning on it. In fact today, the Web channel is by far the most popular route of malware infection into the enterprise.
Until recently the destination websites referenced in the embedded URL links tended to be temporary websites that were setup by the hackers for the sole purpose of infecting visitors. URL filtering list products that most organizations have deployed would offer some protection against this type of attack, if they were frequently updated with the latest infected websites, as they would in effect block the users from visiting the infected website.
Only recently, a serious shift has happened where instead of using their own temporary websites the hackers are now infecting legitimate websites; sites that couldn’t necessarily be blocked or that customers and users need to use as part of their work. This evolutionary shift has weakened the level of protection offered by URL filtering lists and requires new technology and approaches to tackle this increasing issue. In just the first six months of 2009 there has been an increase in excess of 200% of the number of legitimate websites hosting malware. Today, over 75% of all malware hosting websites are legitimate websites. The list of infected websites reads like a Who’s Who of the most popular websites on the Internet, with social networking sites ranking high on the target list.
The process that happens when Blended Threats are delivered is this:
1. The attacker first sets up a target website for their attack, this is the website that hosts the malicious code.
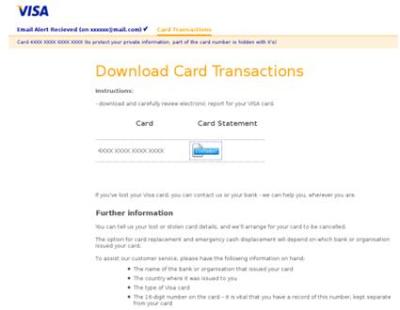
2. Next the attacker sends an email message with an embedded URL link as can be seen from this example:
3. Then when the user clicks on the URL link they browse to the target website which may look like this example:-
4. In this example the Website uses social engineering to try and get the user to download a file where they would get prompted with a false but familiar dialog box like this:
Clicking OK on this box will actually cause the malicious code to be downloaded and executed. Or the attacker might use a ‘drive-by’ method for infection where visiting the website is all that is needed for the infection to occur, typically using some sort of application or browser vulnerability.
So how can we tackle this problem – and where?
All these factors mean that traditional security tools are not detecting these new attacks. The attack vector has evolved, blended threats are just one example and the security tools must evolve too.
There are a number of preventative measures organizations can take. Simple user education or ensuring a good layering of malware detection technologies are only a couple of examples. Security vendors also have a crucial part to play and this session will introduce one of the new innovative techniques for detecting malware that works particularly well with Blended threats.
An example of new innovative techniques is the M86 Security Blended Threats service and the Blended Threats module. The module integrates into M86 Security’s email gateway product – MailMarshal. It extracts any suspicious URL’s from incoming email and forwards them to the Blended Threats service for analysis. The service runs in the cloud and uses M86’s patented Behavioural Analysis technology to look at the actual behaviour of each URL to determine its malicious intent. This approach enables the detection of new and emerging threats without constant updates as it is looking at the actual result or what the link is trying to do rather than trying to identify every single piece of malware as traditional signature based AV scanners do.
This combination of technologies designed to directly address the growing issue of Blended Threats and is in use by our customers today.







 Actu
Actu