The Song Remains the Same: Man in the Mobile Attacks Single out Android
July 2012 by Trusteer
In September 2011, Trusteer reported the first SPITMO (short for SpyEye in the mobile) attack targeting banking customers on the Android platform. Recently Trusteer discovered the first Tatanga-based man in the mobile (MITMO) attack as well as new SPITMO configurations which are targeting Android mobile banking users in Germany, the Netherlands, Portugal and Spain. With nearly 60 percent of the market and a reputation for weak app security, it’s no surprise that Android has become the preferred target for financial malware.
Like previous attacks, both the SPITMO and Tatanga MITMO variants target Windows users on the web and use a web injection in the desktop browser to lure them into installing a fake security application on their phones. The fraudsters claim this application is required by the bank as a new layer of protection, and that 15 million bank customers around the world are already using it.
The victims are asked to choose the device’s operating system from the following list:
iOS (iPhone)
BlackBerry
Android (Samsung, HTC, etc.)
Symbian (Nokia)
other
In most attacks, if the victim is using an operating system other than Android the malware informs the user that no further action is required. However, for all Android users, the desktop component of the MITMO attack requests the victim’s phone number and notifies them that a link for downloading the security application has been sent (via SMS) to their mobile device. The user is directed to install the fake application from this link and enter the activation code provided by the malware. Certain attacks also request that BlackBerry users download the application, but it does not actually install on these devices.
Once installed, the mobile malware captures all SMS traffic, including transaction authorization codes sent by the bank to the victim via SMS, and forwards them to the fraudsters. This enables the criminals to initiate fraudulent transfers and capture the security codes needed to bypass SMS-based out-of-band authorization systems used by many European banks.
The attackers use different social engineering tricks in each country to lure victims into downloading the fake application, including URLs with the words “secure” and “Android files” with a .com domain name.
Trusteer investigated the registration information for these URLs, which were located in China and the US. They were registered in June just prior to the initial attacks. All URLs are inactive at this moment.
Both Tatanga and SpyEye use the same android application in this attack.
Spanish Bank Customer Attacks
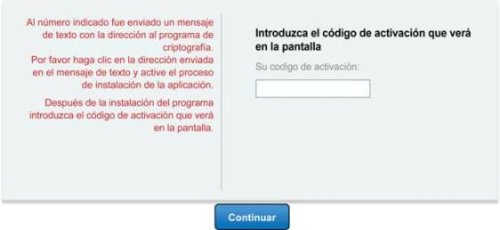
In the attack on Spanish banks, the victims are asked to download the security application from a link in an SMS sent to their mobile phones..
Here is a screen capture of the message displayed to the victim during their online banking session:
The message mentions that bank has taken steps to protect its customers against attacks on mobile devices and requires the user install the application.
The malware then asks the Android users to submit a code they received with the text message to activate the application:
BlackBerry users are notified that the security application has been installed successfully, although it only installs on Android devices.
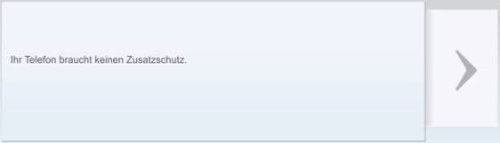
Victims that use other mobile operating systems are notified that their device does not require this special security measure:
German Bank Customer Attacks
In the German attacks, criminals lure victims into downloading the fake application by claiming the bank has developed special security measures in cooperation with Oracle. The fraudsters claim that more than 15 million bank customers around the world already use the system.
Android users are asked to download the security application from a link sent by the malware via an SMS, and to submit the activation code on the bank’s (spoofed) web page:
As in the Spanish attack, BlackBerry users are notified that the application was successfully installed and that they are protected, although no installation actaully takes place.
Meanwhile, victims that use other mobile operating systems are notified that their device does not require any additional security.
This discovery confirms that Man-in-the-Mobile attacks are focusing primarily on Android devices. Multiple studies show that Android devices account for more than 60% of smartphone market in the targeted countries (Spain, Portugal, Germany and the Netherlands). Android popularity and the relative ease of developing and distributing Android applications are probably the reasons why Cybercriminals have singled out this particular platform for mobile malware attacks.
“Once fraudsters have infected a victim’s web and mobile endpoints, very few security mechanisms can prevent fraud from occurring,” said Trusteer CTO Amit Klein. “Trusteer can secure against Man-in-the-Browser malware such as SpyEye and Tatanga infections that convince users to install MITMO on their mobile devices. Trusteer Pinpoint remotely detects Man-in-the-Browser malware on any device and drives mitigation activities. Trusteer Rapport installed on PC and Mac endpoints blocks and removes Man-in-the-Browser malware. Trusteer Mobile installed on Android and iOS devices (standalone or as part of an online banking mobile app) can detect and support the removal of mobile malware such as the malware used in this attack.”
Today, criminals are compromising Android devices to circumvent out-of-band security mechanisms that send SMS messages to authorize both web and mobile banking transactions. Going forward, Trusteer expects criminals to expand their attack tactics on mobile devices to mimic desktop attack techniques, including web injection, key loggers, and screen capture, among others.







 Actu
Actu